思维导图
源码分析
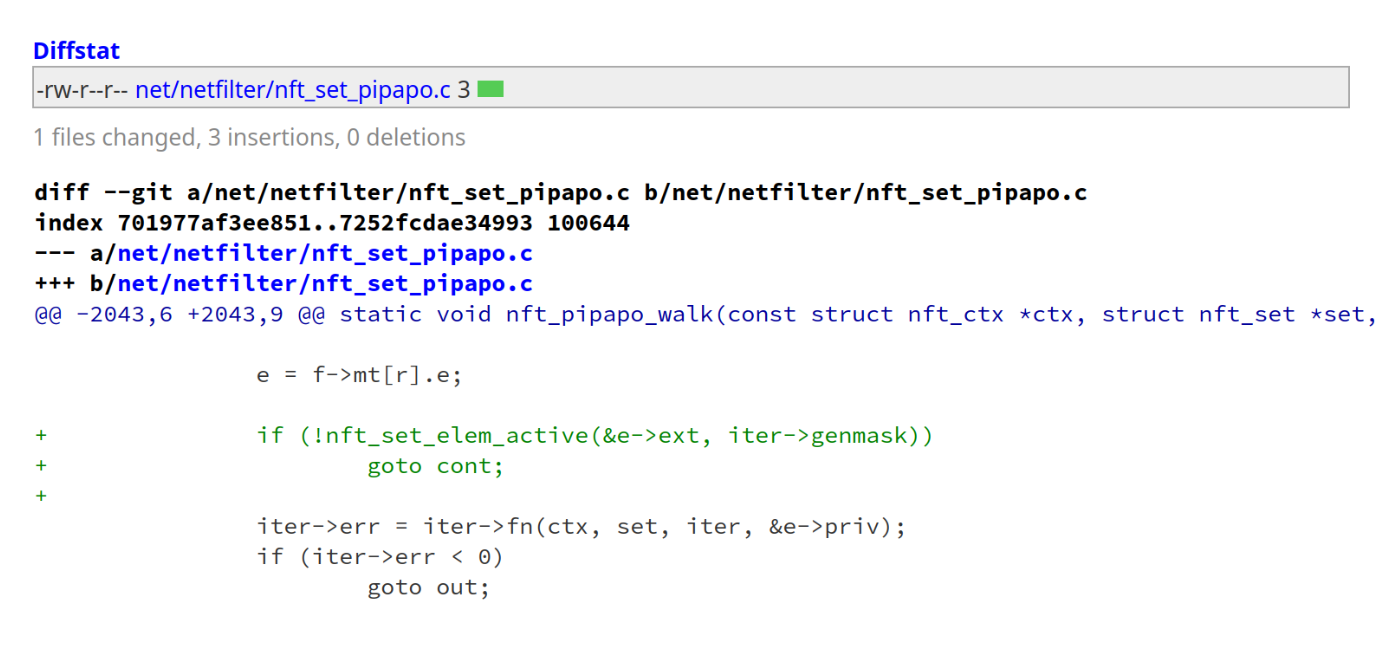
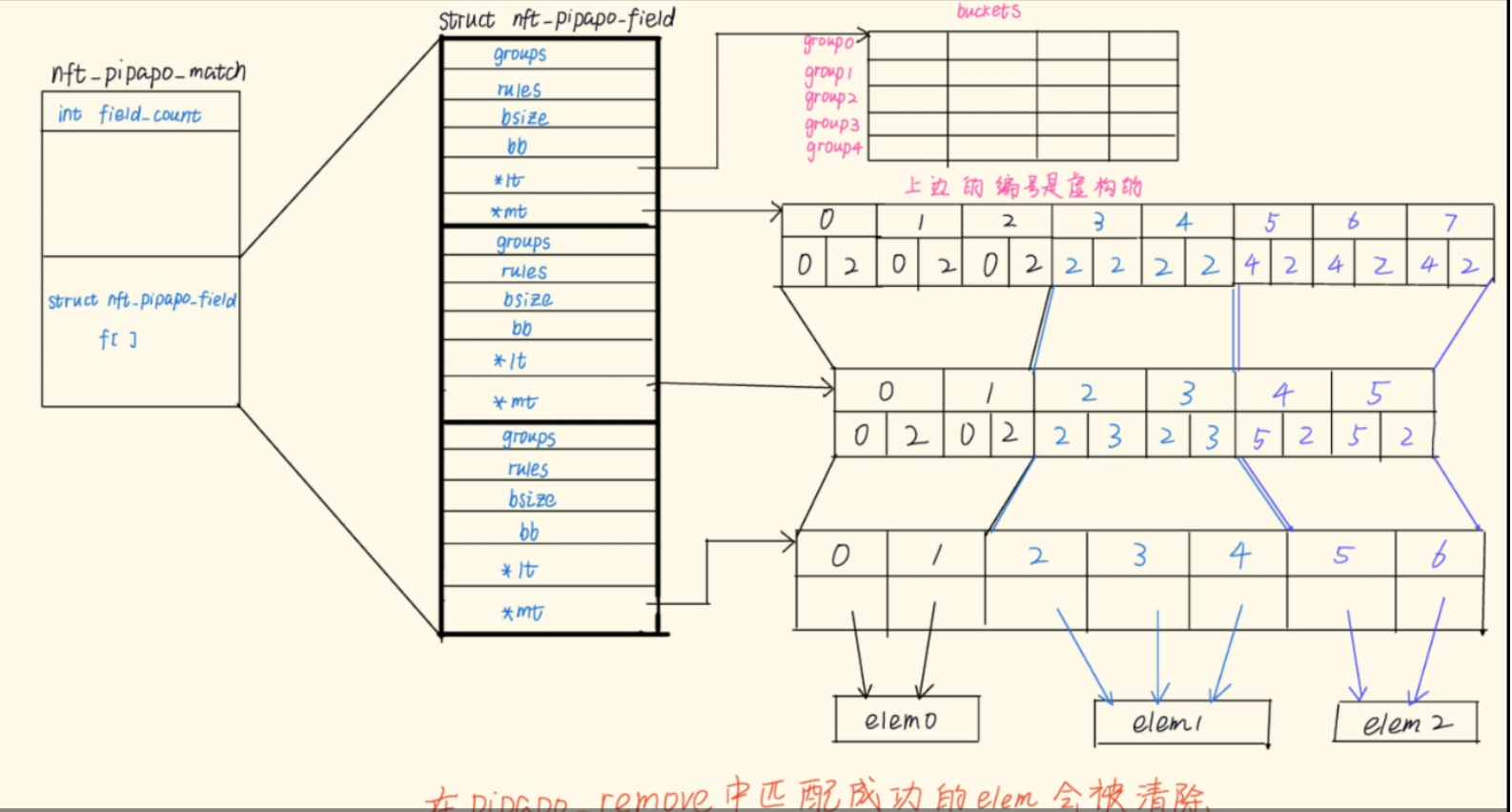
pipapo_walk
源码链接:https://elixir.bootlin.com/linux/v5.15.185/source/net/netfilter/nft_set_pipapo.c#L2041
static void nft_pipapo_walk(const struct nft_ctx *ctx, struct nft_set *set, |
总结一下,pipapo_walk函数的作用就是以一个iter作为参数的集合传进来,然后遍历pipapo_set中的每一个elem,并且各自调用iter中的回调函数fn一次;
下面看一下哪些函数会调用到walk,以及传入的回调函数指针fn都是什么:
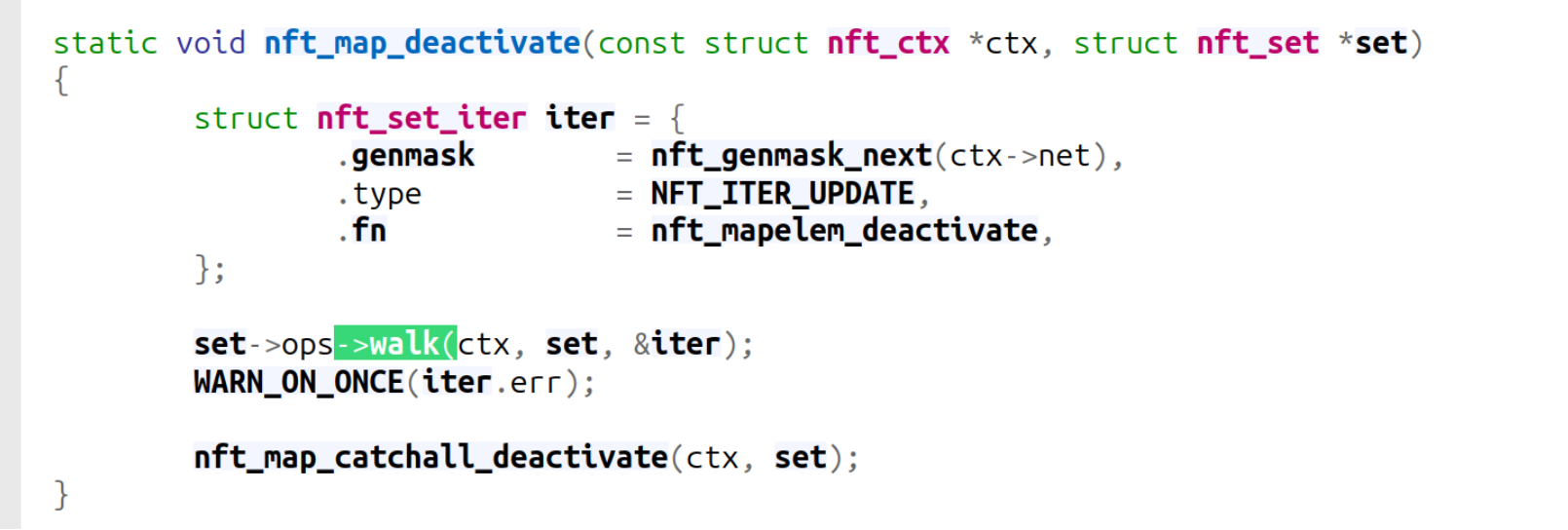
nft_map_deactivate:
nf_tables_bind_set:
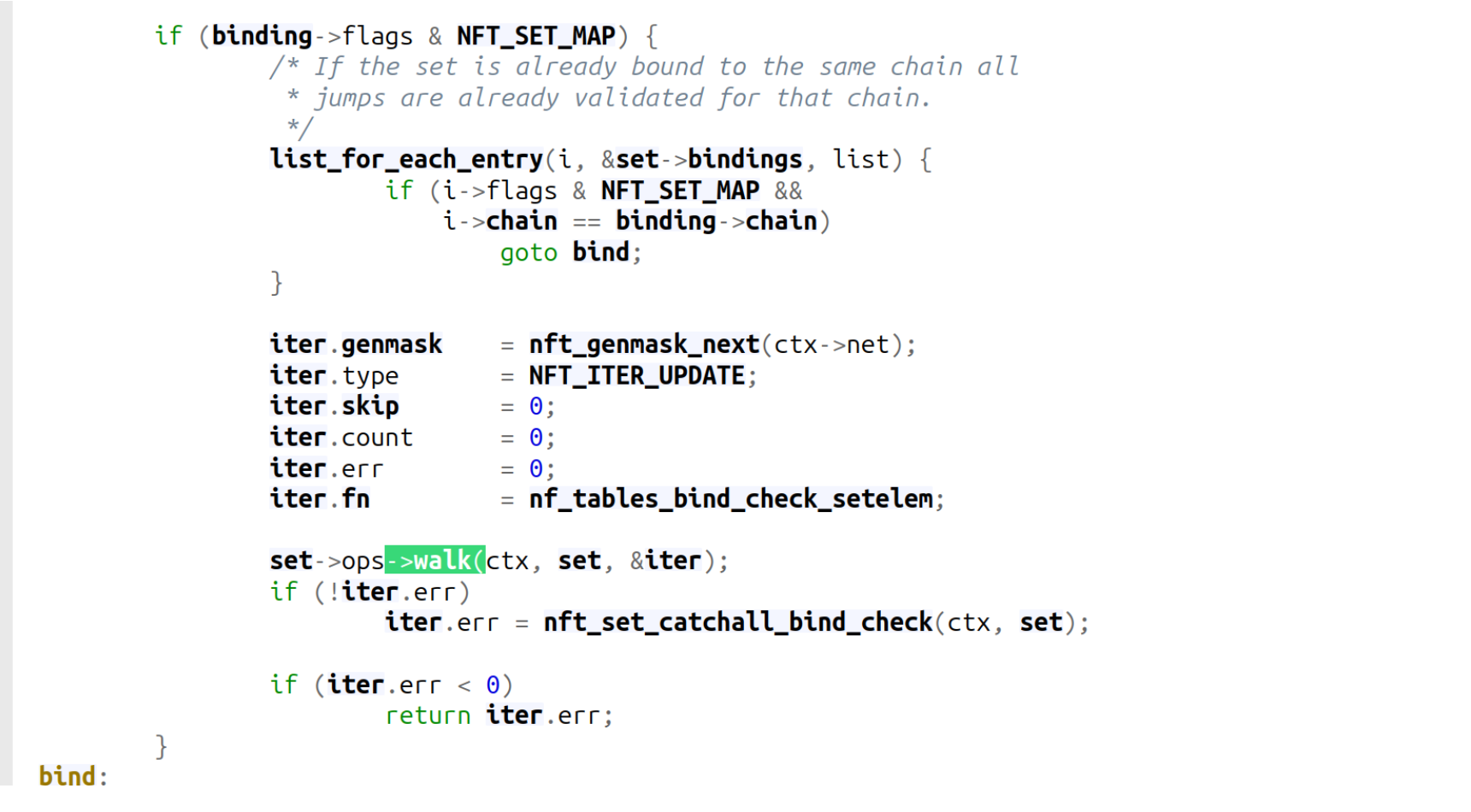
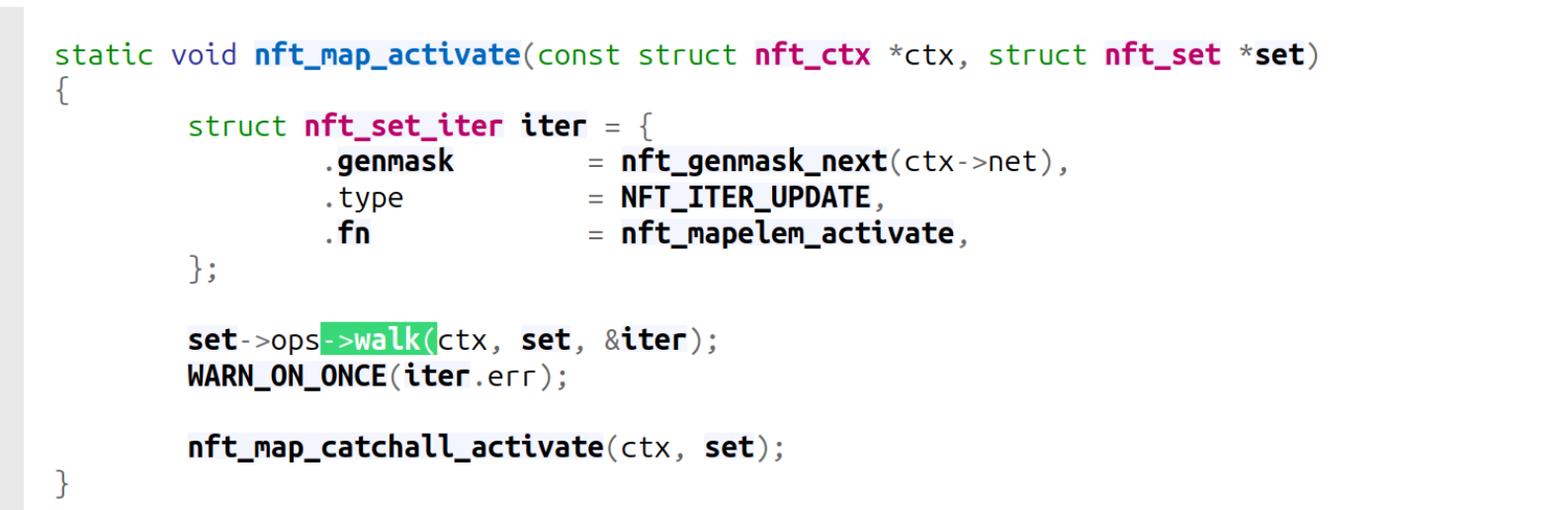
nft_map_activate:
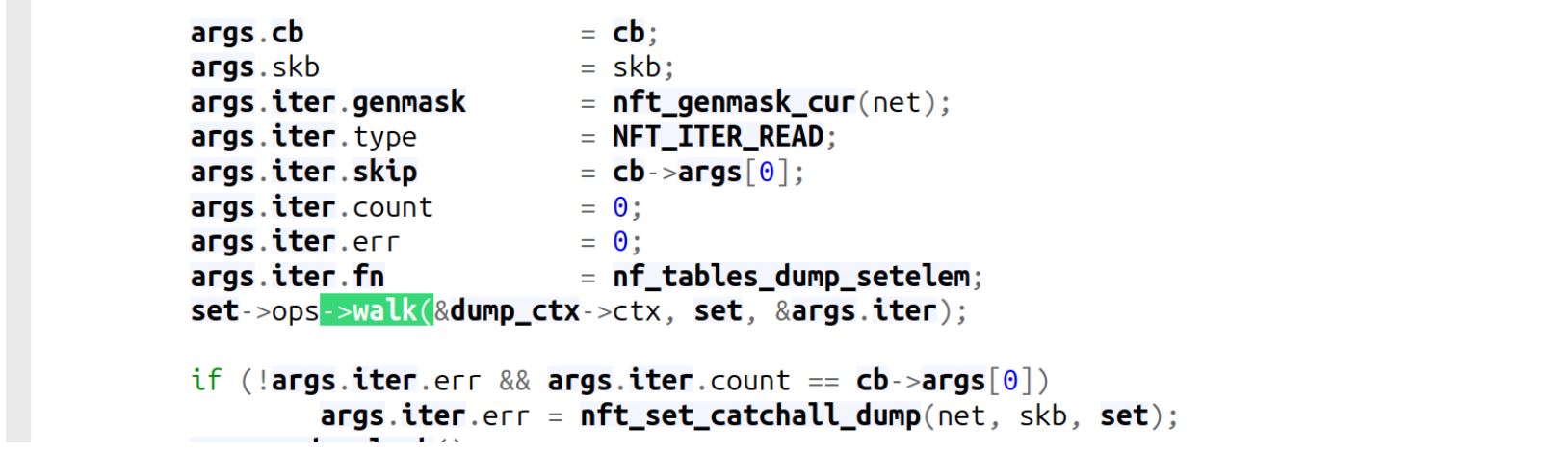
nf_tables_dump_set:
nft_set_flush:
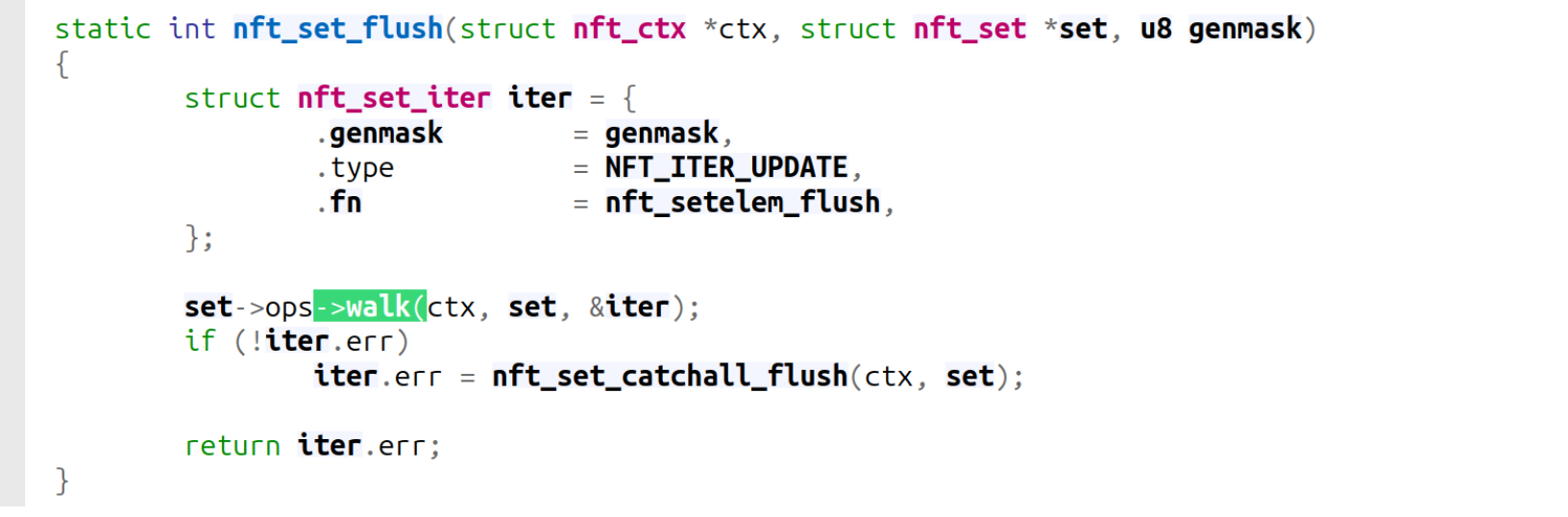
nft_setelem_flush
static int nft_setelem_flush(const struct nft_ctx *ctx, |
nft_pipapo_flush
static bool nft_pipapo_flush(const struct net *net, const struct nft_set *set, |
static void *pipapo_deactivate(const struct net *net, const struct nft_set *set, |
static inline void nft_set_elem_change_active(const struct net *net, |
static struct nft_pipapo_elem *pipapo_get(const struct net *net, |
nf_tables_delsetelem
static int nf_tables_delsetelem(struct sk_buff *skb, |
nft_del_setelem:
static int nft_del_setelem(struct nft_ctx *ctx, struct nft_set *set, |
环境搭建
commit:
8bb7eca972ad531c9b149c0a51ab43a417385813 |
config:
CONFIG_USER_NS=y |
POC
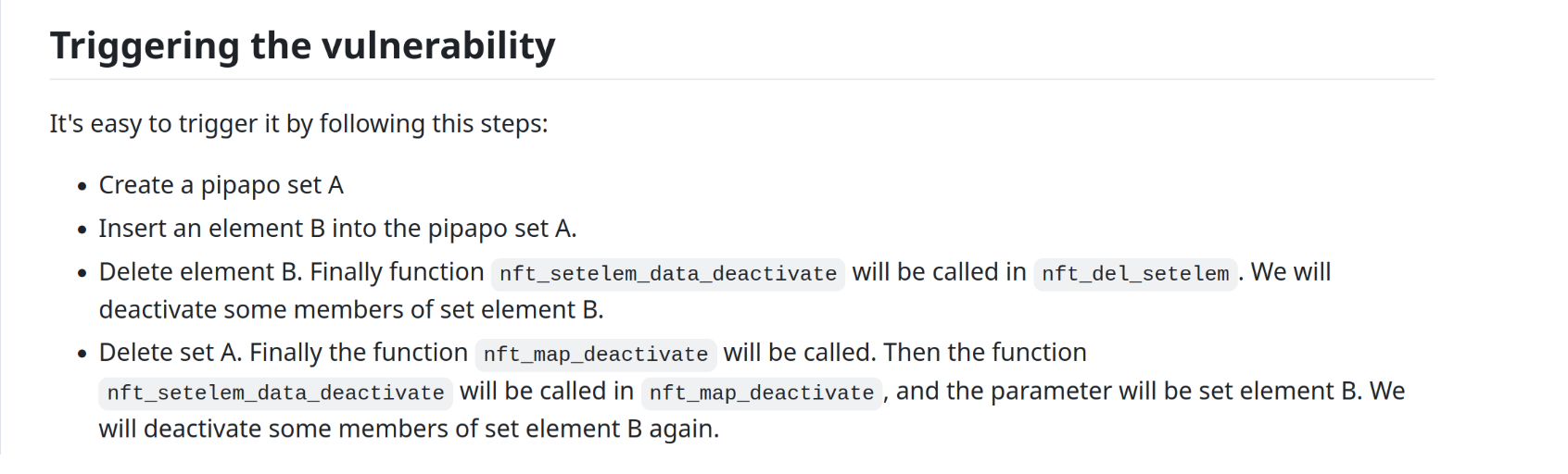
nft_set_flush的调用链如下:
|
不能flush两次,



